ISO 27001: the international information security standard
The fundamentals of the ISO 27001 standard
ISO 27001 represents the international reference standard for information security management. This standard requires the establishment of a comprehensive Information Security Management System (ISMS) that structures the security approach in a systematic and verifiable manner.

Certification is an ongoing process. Certified organizations are subject to regular independent audits who verify that the ISMS is working effectively and improving according to the PDCA cycle: Plan (plan security goals), Do (implement controls), Check (check effectiveness), Act (improve continuously). The current version ISO/IEC 27001:2022, published in October 2022, is gradually replacing the 2013 version.
This certification meets several critical issues. In fact, the RGPD imposes fines of up to 2% of global turnover (or 10 million euros) for certain offenses, and up to 4% of annual global turnover (or 20 million euros) for the most serious violations. Because of all this, your B2B customers require contractual guarantees in the face of constantly evolving cyber threats.
The 4 themes and 93 controls in Appendix A
The 2022 version of ISO 27001 has modernized the organization of security controls. Appendix A now includes 93 controls organized in 4 main themes.
Organizational controls define policies, governance, and human resources management. Controls related to people, on the other hand, address user awareness, training and responsibilities. For their part, the physical checks protect installations and equipment. As for technological controls, they cover access control, cryptography, vulnerability management, and surveillance.
For cloud environments, several controls are of particular importance:
- Access control defines who can access what resources, with strong authentication and privilege management mechanisms.
- Cryptography protects data in transit and at rest.
- Incident management Establishes processes to quickly detect and respond to threats
- Business continuity ensures that your systems remain available even in the event of a disaster.
Note that in a Dynamics 365 environment, ISO 27001 imposes fine management of permissions with separation of roles, traced and justified administrator accesses, available multi-factor authentication and inactive sessions that expire automatically.
ISO 27001 in the security certification ecosystem
SOC 2 Type II certification complements ISO 27001 by auditing operational controls over an extended period of time, proving that the system works effectively over time. Second, theISO 27017 extends ISO 27001 with additional controls specific to cloud services, while ISO 27018 focuses on the protection of personal data in the cloud.
Some sectors require specific certifications. Thus, HDS (Health Data Hosting) is mandatory in France for any host that processes health data. Microsoft offers HDS certified Azure services.
Another example: PCI DSS is required to process credit card data knowing that Microsoft has PCI DSS certificates for certain services and specific components.
Moreover, it should be noted that the Microsoft ecosystem counts over 90 certifications to meet all sectoral regulations.
Scope and scope of ISO 27001 certification at Microsoft
Services and infrastructure covered by certification
Microsoft's ISO 27001 certification covers the entire cloud ecosystem that you use every day for consistent security across all your tools. In fact:
- Azure benefits from certification for all of its infrastructure (IaaS) and platform (PaaS) services.
- Microsoft 365 is certified in its entirety, including Exchange Online, SharePoint Online, and Teams.
- Dynamics 365 in all its forms (Sales, Customer Service, Finance, Supply Chain Management) is covered.
- Power Platform as a whole (Power Apps, Power Automate, Power BI, Dataverse) also falls within the certified scope.
This certification extends geographically to all Microsoft data centers in the world, with over 60 regions covered. For example, European data centers are all ISO 27001 certified, making it possible to meet data sovereignty requirements.
Microsoft is subject to comprehensive annual audits conducted by accredited independent organizations. The resulting certificates can be viewed on the Service Trust Portal from Microsoft.
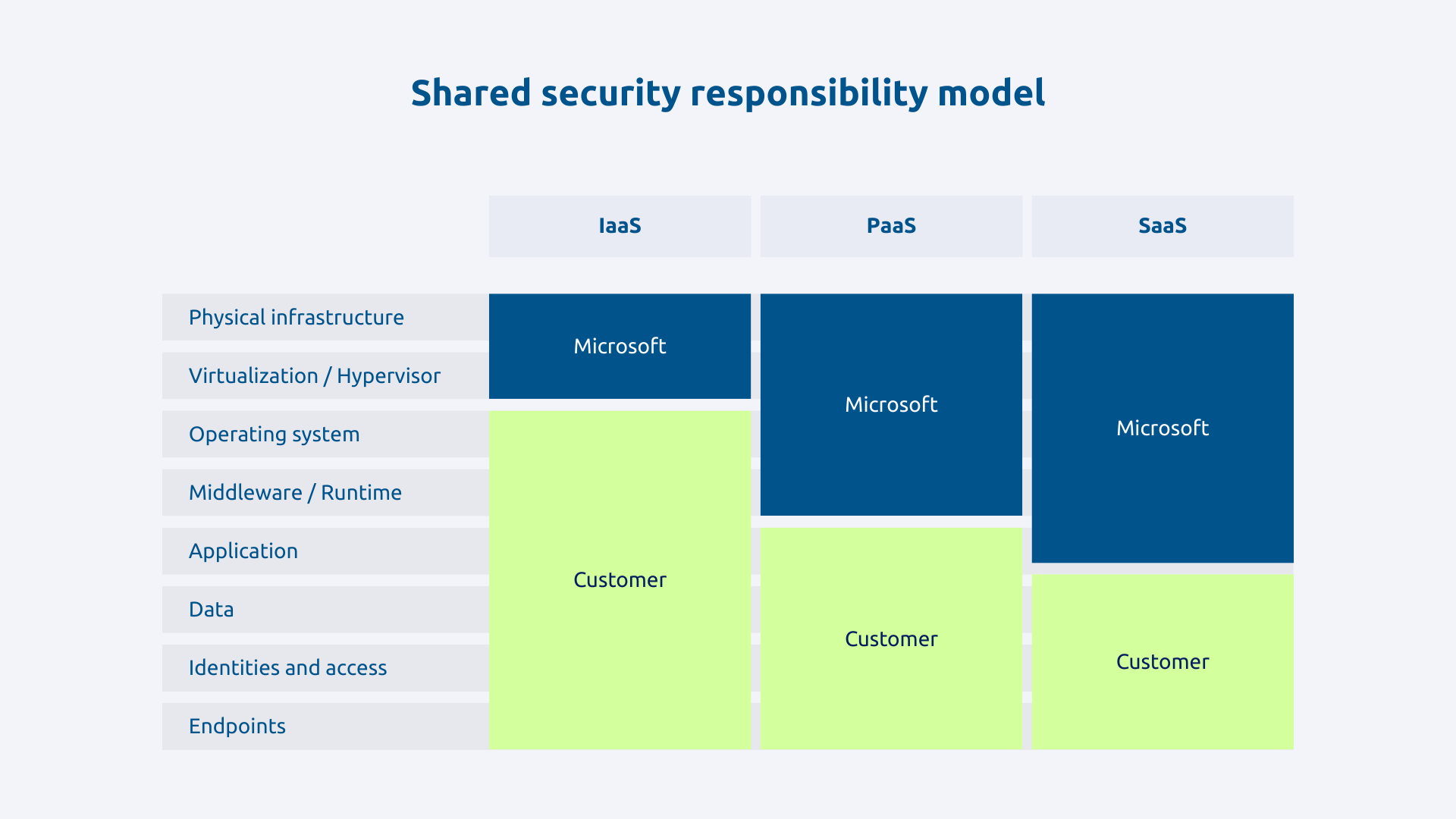
The shared responsibility model in the cloud
That said, Microsoft's ISO 27001 certification does not exempt you from your own responsibilities. Also, understand the shared responsibility model is it essential to avoid security breaches.
For Infrastructure as a Service (IaaS), Microsoft manages the physical infrastructure, network, and hypervisor, while you remain responsible for the operating system, applications, and data. For the Platform as a Service (PaaS), Microsoft adds OS and middleware management. For the Software as a Service (SaaS) like Dynamics 365, Microsoft also manages the application.
Some responsibilities remain always at your expense. These include:
- identity and access management: you define who has access to what, who activates multi-factor authentication, who manages roles;
- configuring security controls is your responsibility: Data Loss Prevention, retention policies, encryption rules;
- the protection and classification of your data.
The certification covers the Microsoft part rigorously. But your final compliance depends on your own configuration. This is where the support of an expert integrator like Askware makes all the difference.
Microsoft security governance and continuous improvement
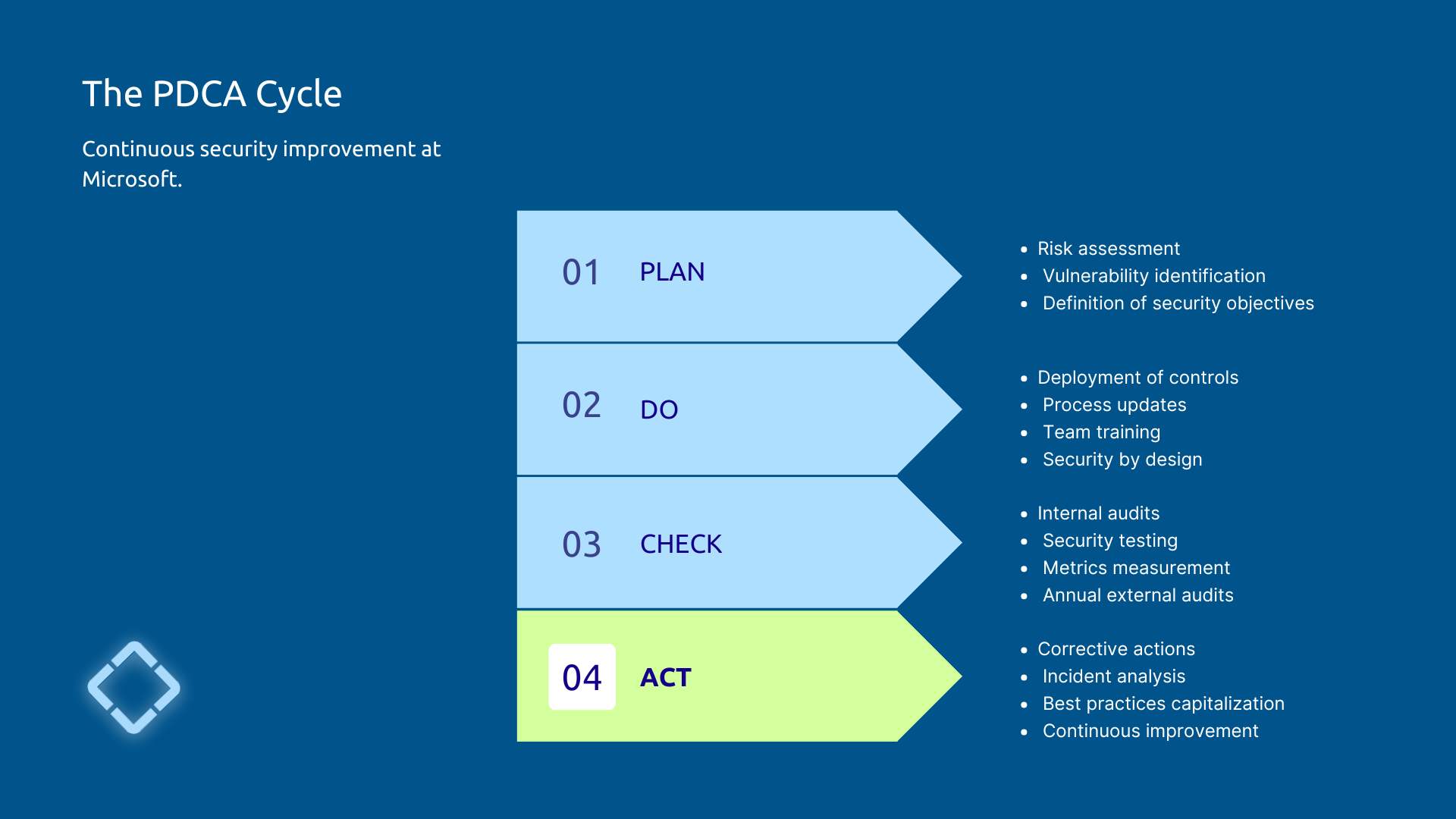
The PDCA cycle applied to security
As mentioned at the beginning of the article, ISO 27001 certification requires Microsoft to apply a continuous improvement process based on PDCA cycle :
- The phase Plan assesses security risks on a regular basis. Microsoft analyzes new threats, identifies potential vulnerabilities, and sets priority goals.
- The phase Do Implements controls: deploying new protection mechanisms, updating processes, training teams, security by design.
- The phase Check check the effectiveness of the controls. Microsoft conducts internal audits, performs security tests, and measures performance indicators. Annual external audits are the ultimate validation.
- The phase Act draw conclusions to continuously improve the system. Discrepancies give rise to corrective actions, incidents are analyzed to prevent their recurrence.
Proactive approach and threat management
Beyond compliance, Microsoft is investing in proactive approach that anticipates threats.
Patch Management is a crucial part of this strategy. Microsoft regularly releases security patches that are rigorously tested before deployment. For critical vulnerabilities, off-cycle patches can be urgently released.
Threat intelligence is based on data collected across the Microsoft ecosystem. With its large installed base and the colossal network traffic flowing through its services, Microsoft has unique visibility into the threat landscape. This collective intelligence feeds detection systems and makes it possible to quickly identify new attack techniques.
Red team/Blue team exercises regularly simulate real attacks to reveal flaws and improve detection and response capabilities.
In the event of an incident affecting services, a formal notification process promptly informs customers with details about the incident and ongoing corrective actions. Microsoft is also publishing Transparency Reports that document data access requests and statistics on detected threats.
ISO 27001 and regulatory compliance: guarantees and limits
Personal data protection and sovereignty
ISO 27001 covers technical aspects : how to protect data against unauthorized access, loss, alteration. For its part, the RGPD formulates legal requirements : purpose of the treatment, limitation of storage, rights of individuals, documentation of treatments. The two complement each other but do not replace each other.
Microsoft provides several guarantees to facilitate your GDPR compliance. First of all your data can be stored in European datacenters with the commitment that they will not be transferred outside the EU without explicit instructions.
Then there's the Data Processing Addendum (DPA), which defines the role of subcontractor. Therefore, Microsoft is committed to processing data only according to your instructions, to implementing appropriate security measures, and to assisting you in exercising individual rights.
Likewise, Microsoft tools provide technical capabilities to exercise GDPR rights. Purview identifies where personal data is located. Search and export functionalities facilitate responses to access requests. Deletion capabilities make it possible to respect the right to erasure. The logs track accesses.
Your responsibilities for full compliance
As a reminder, several responsibilities remain your responsibility.
Among the latter, there is the configuring classification tools : Purview Information Protection allows you to define sensitivity labels, but you are the one who must define your taxonomy, create labels, and train your users.
In order to prevent inappropriate sharing, you should also define what constitutes sensitive data in your context and create the corresponding rules. These are the Data Loss Prevention policies.
In the same way, you will not be able to do without data governance. In other words, you'll need to designate data owners, define validation processes for access requests, and establish retention policies.
For your business users to be able to understand the challenges and know how to use the tools available, you must take care of the team training.
Finally, the law requires you to document treatments and therefore to maintain a register of processing activities.
In short, Microsoft provides ISO 27001 certified bricks, but your compliance depends on their expert assembly and integration into coherent governance.
Operational security in your Microsoft projects
Secure integrations and automations
Power Platform and Azure allow you to connect your applications, but these integrations also create potential attack surfaces.
Let's start with the API and connector security, which is a major challenge. Power Platform offers today over 1,300 connectors in its complete catalog. Microsoft distinguishes several categories: Standard connectors included in the basic licenses, the Premium connectors requiring additional licenses, and the Custom connectors developed for specific needs.
Then the encryption protects your information at every level. All communication between your users and Microsoft services uses TLS 1.2 or higher. At the same time, data stored in Azure, Dataverse, or Microsoft 365 is encrypted at rest with AES-256. For particularly sensitive data, you can even add an extra layer of protection with your own keys managed through Azure Key Vault.
By the identity and access management Through Microsoft Entra ID, you apply Zero Trust principles. In this approach, each access is systematically checked, even from the internal network. Multi-factor authentication adds a layer of protection against password theft, while the principle of least privilege ensures that each user only has access to the resources that are strictly necessary.
Beyond these basic mechanisms, several advanced security features need to be activated and configured. We already talked about Data Loss Prevention but Conditional Access allows you to define contextual rules. There is also Azure Key Vault, which centralizes the management of secrets, keys and certificates, avoiding their dissemination in plain text in scripts and configurations.
Finally, the Audit Trails track all significant events and are essential for detecting anomalous behavior, investigating incidents, and demonstrating compliance in the event of an audit.
Business Continuity and Resilience
Microsoft maintains business continuity plans (BCP) and resumption of activity (DRP) for all of its services. These plans are tested regularly through exercises that simulate various crisis scenarios, and the results of these tests feed into the continuous improvement of procedures.
On a technical level, the backup strategies are fully automated. Your Dynamics 365, SharePoint, and Exchange data is thus backed up daily with several restore points available. These backups are also replicated geographically to protect against the complete destruction of a site.
Microsoft formalizes its commitments through Availability SLA (Service Level Agreement) that contractually guarantee a minimum level of availability. The typical commitment is 99.9% availability for most services, which represents approximately 8.76 hours of maximum downtime per year.
To strengthen this resilience, the geographic redundancy Data centers protect against localized disasters. In fact, Azure organizes its datacenters into paired regions: two geographically distant regions that replicate each other. In concrete terms, if a data center suffers a major outage, your applications can automatically switch to the twin data center, thus minimizing the interruption of service.
However, be careful: Microsoft guarantees do not exempt you from having your own continuity plan. In particular, you must define your RTO (Recovery Time Objective - maximum acceptable time to put a service back online) and RPO (Recovery Point Objective - maximum age of lost data acceptable). These goals then determine your configuration choices. It is also imperative to test these procedures regularly to verify that your teams know how to react in a real situation.
Microsoft's ISO 27001 certification is a solid guarantee. But the shared responsibility model means that an essential part remains your responsibility: configuration, governance, access management, training. Askware combines technical expertise in the Microsoft ecosystem and an understanding of compliance issues to support you from initial audit to ongoing operation.
Is your environment making full use of ISO 27001 guarantees? Askware offers you a compliance audit to permanently secure your platform.