Shadow IT: understanding the phenomenon before fighting it
What is shadow IT and why is it emerging?
Shadow IT refers to all of technologies, software, applications, or services used within an organization without formal approval from the IT department. This practice takes many forms:
- SaaS applications subscribed with a professional bank card;
- personal devices used to access company data;
- consumer cloud services hijacked for business purposes.
Why is this phenomenon exploding? Digital transformation requires business teams to adapt quickly, but traditional IT processes remain slow and rigid. For example, a marketing team that has been waiting for 3 months for an evolution of its official CRM and that ends up adopting a SaaS tool, operational in 20 minutes.
User experience of consumer tools is no stranger to all this, in fact, it promises employees simple and immediately operational applications. Therefore, if the IT department offers complex tools, the gap becomes difficult for the teams concerned to accept.
In fact, shadow IT is often a legitimate response to a real problem.
The real (and often underestimated) risks of shadow IT
However, the consequences of shadow IT can be dramatic.
Thus, the security risks are on the front line. Unapproved tools have flaws that the IT department cannot detect or correct. Multi-factor authentication is rarely enabled, and sensitive data flows on platforms you don't know existed.
In terms of compliance, the GDPR imposes strict obligations. A shadow IT tool that hosts customer data outside the European Union, without an appropriate processing agreement, directly exposes your company to sanctions of up to 4% of global annual turnover.
Data silos represent another scourge insofar as each tool creates its own repository. The same customer information exists in the official CRM, in the unauthorized marketing tool, and in the support solution. Result: inconsistencies, duplicates, impossibility of having a unified view.
As a result, the hidden costs accumulate: duplicate licenses, operational inefficiencies, IT time consumed resolving incidents on unknown platforms. In fact, shadow IT can generate significant additional costs compared to managed IT expenses.
Finally, the loss of visibility for the IT department weakens the entire architecture. How do you plan a cloud migration when you don't know all the tools in production? Shadow IT transforms your information system into a shadow zone where risks thrive: undetected security breaches, incidents without traceability, impossibility of guaranteeing regulatory compliance.
Why the simple ban doesn't work
A strict blocking policy generates Frustration among business teams who feel restricted. This frustration is deteriorating relationships between IT and the rest of the business. Businesses perceive the IT department as an obstacle rather than a partner.
Even worse, the ban encourages shadow IT: teams continue to use unauthorized tools, but in secret.
Let us imagine the case of a major European bank. Faced with the multiplication of SaaS tools, the IT department has blocked access to all non-referenced cloud applications. Six months later, an audit revealed that Shadow IT had exploded. Employees were using their personal devices and 4G connections, creating an attack surface that was even more difficult to control.
In a context of cloud and generalized mobility, the technical blockage is becoming an endless race. New services are appearing every day. You can't block everything without paralyzing the business.
In short, this approach tends to slow innovation.
The 4 pillars of balanced IT governance
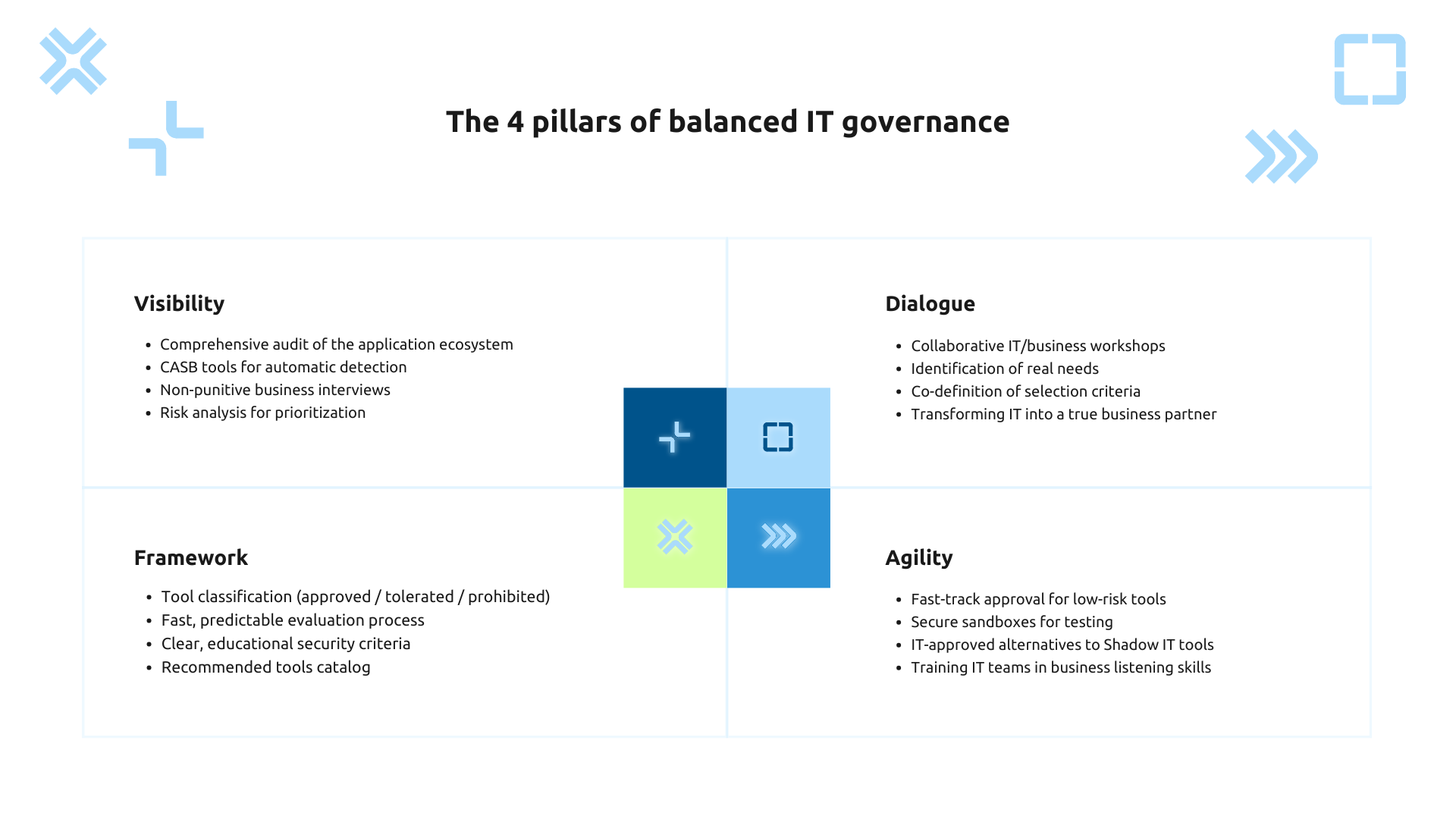
Visibility: mapping the existing without judgment
You can't manage what you can't see. The first step is to establish a comprehensive but benevolent audit of your real application ecosystem.
This mapping combines several methods:
- Network flow analysis reveals connections to external services, a first step towards a Zero Trust architecture.
- Cloud Access Security Broker (CASB) tools automatically detect the SaaS applications in use.
- License audits identify subscriptions purchased with business cards.
- Direct interviews with business teams remain irreplaceable. These exchanges reveal the real uses, the reasons for choosing this or that tool, the difficulties encountered with official solutions.
The approach must be non-punitive. If employees fear sanctions, they will hide their practices and the audit will be incomplete. Position the approach as an opportunity to improve the IT offer: “We want to understand your needs in order to better meet them, not punish you.”
A shadow IT audit follows three steps:
- automatic scan via CASB for technical mapping;
- craft workshops by department to qualify uses;
- risk analysis to prioritize actions.
Dialogue: understanding real business needs
Behind every shadow IT tool is an unmet business need. Understanding this need is the key to offering acceptable alternatives.
This understanding goes through collaborative IT/business workshops. Business teams explain their operational constraints, their business objectives. IT presents the challenges of security, architectural coherence and compliance.
These workshops should focus on real use cases. Ask the teams to describe in concrete terms what they are doing with the unauthorized tool.
Co-define the selection criteria of tools. What functionalities are non-negotiable for businesses? What level of simplicity is expected? On the IT side, what security standards are imperative?
This dialog makes it possible to identify Quick Wins : shadow IT tools that can be quickly regularized because they are securable and meet a critical need. Instead of blocking them violently, you integrate them into the official ecosystem after technical hardening.
The framework: define a clear and accessible policy
This policy starts with a Classification of tools into three categories. The approved tools have passed all security and integration validations. Tools that are tolerated under certain conditions can be used within a limited area. Prohibited tools present unacceptable risks.
Define a rapid assessment process for the new tools. As a best practice, some organizations define internal SLAs with predictable response times: for example, fifteen days for low-risk tools, one month for critical tools. This predictability changes perception.
Communicate them safety criteria in an educational way: “We ask that the data be hosted in Europe because the RGPD requires it. We require encryption because a leak could compromise our business.”
Create a recommended tool catalog by use: collaboration, project management, marketing automation. For each category, suggest two or three validated solutions. This approach provides flexibility while maintaining control.
A decision matrix structures arbitration: risk versus business value. Tools with low risk and high value are approved quickly. Those with high risk and low value are refused.
Agility: facilitating supervised innovation
To sustainably reduce shadow IT, offer businesses a faster and more flexible alternative to wild solutions.
One fast certification process for low-risk tools defuses the main motivation of shadow IT. A fast-track course validates a standard SaaS tool that meets security standards in a few days.
Secure sandboxes allow new tools to be tested in a controlled environment. Isolated from the production network, they offer enough freedom to experiment before formal certification.
IT must Suggest alternatives to the most requested shadow IT tools. If three departments each use a different project management tool that is not authorized, your official offer is failing. Invest in a modern solution that meets these needs.
Train your IT teams in listening to business needs. Understanding business challenges and translating business requests into technical specifications creates an indispensable bridge.
How to regain control gradually and sustainably
Step 1: Audit and risk prioritization
Regaining control starts with a methodical inventory leading to a prioritized action plan.
Combine multiple tools. A CASB like Microsoft Defender for Cloud Apps detects cloud applications through network analysis. Structured interviews with business managers complete the technical vision. In many organizations, an initial audit can take 4 to 6 weeks, depending on the size and complexity of the information system.
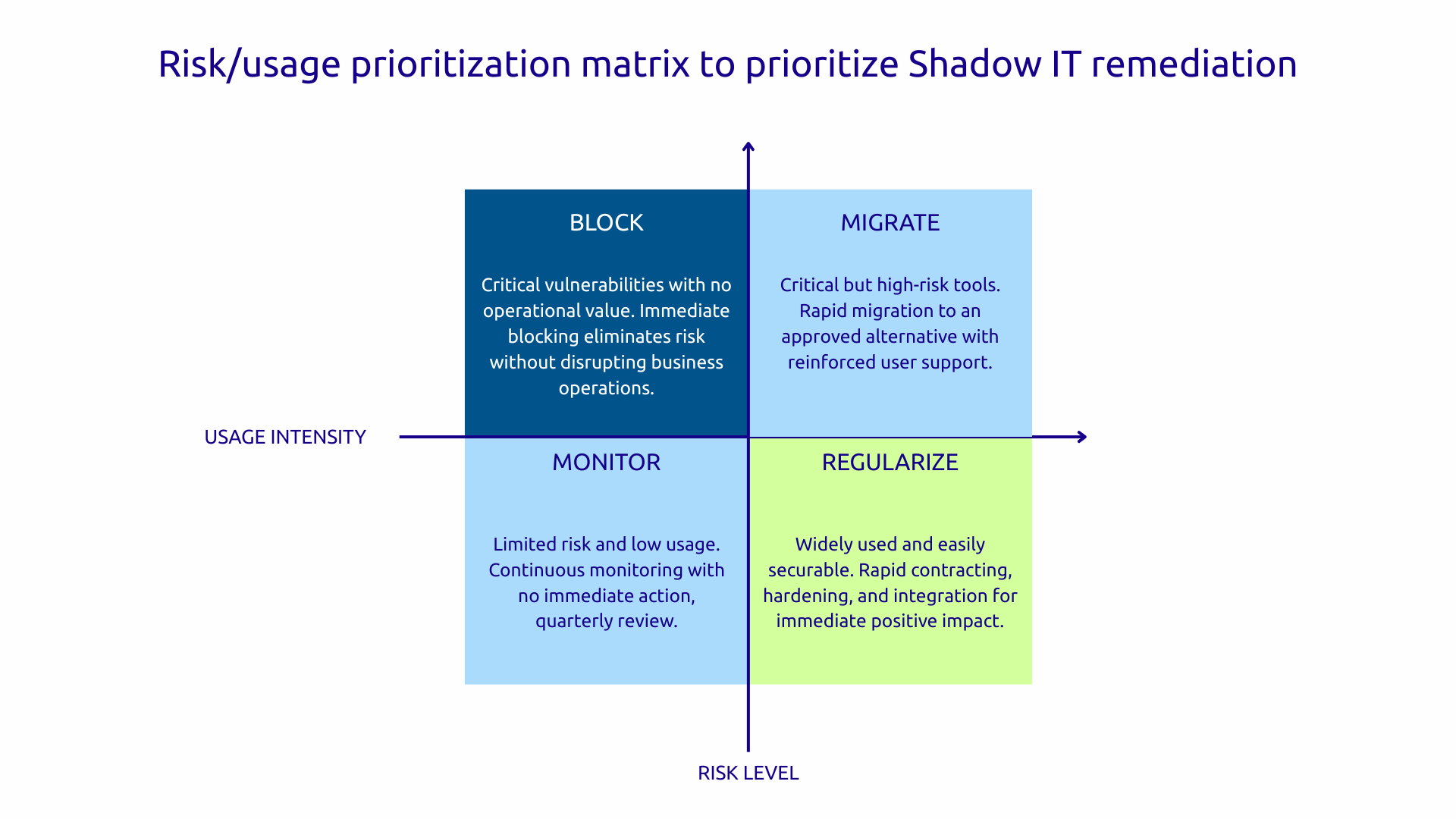
Prioritization is becoming crucial. Build a risk/use matrix that positions each tool detected according to the level of risk and the intensity of use.
This matrix reveals the Quick Wins : widely used tools that present a moderate risk can be quickly secured and regularized, bringing significant improvement. Conversely, a tool that is rarely used but very risky can be blocked without major operational impact.
Step 2: regularization and migration of critical tools
For the shadow IT tools that you decide to keep, the regularization process turns them into official tools.
This regularization involves the contractualization with the editor to clarify responsibilities and service levels. Then the safe hardening : activation of multi-factor authentication, configuration of access policies, encryption, connection to monitoring systems.
The mainstreaming with the existing ecosystem connects the tool to the centralized authentication system via Microsoft Entra ID for automatic account provisioning.
In some cases, you have to migrate to an approved solution. This migration requires careful support. Identify power users and train them as a matter of priority. They will become your ambassadors. Plan for a transition period where the two tools coexist.
Communicate clearly: “We're replacing tool X with tool Y because it offers the same functionalities, plus native integration, better security, and professional support.”
Step 3: the establishment of ongoing governance
Once the critical tools have been treated, the real challenge begins: to prevent Shadow IT from reappearing. Governance must in fact become a permanent process.
This permanence is based primarily on automated tracking mechanisms. A centralized dashboard displays key indicators in real time: number of cloud applications detected, coverage rate by approved tools, security incidents, average request processing time. Complete this monitoring with automatic alerts which are triggered as soon as an anomaly appears: connection to a new service that is not referenced, unusual peak in use, risk threshold exceeded.
But technology alone is not enough. Also maintain a regular IT/business dialogue. Organize quarterly committees to review the application ecosystem. Name some IT ambassadors in each business department to continuously report needs and facilitate the adoption of best practices.
Finally, don't forget to change your policy according to field feedback. Rigid governance is rapidly becoming obsolete. Business needs are changing, new tools are emerging, security standards are evolving. Your framework needs to adapt continuously to remain relevant.
Shadow IT governance is a dynamic balance that requires vigilance, listening and constant adaptation.
Power Platform and Azure: Microsoft's answer to shadow IT
Low-code/no-code as an alternative to shadow IT
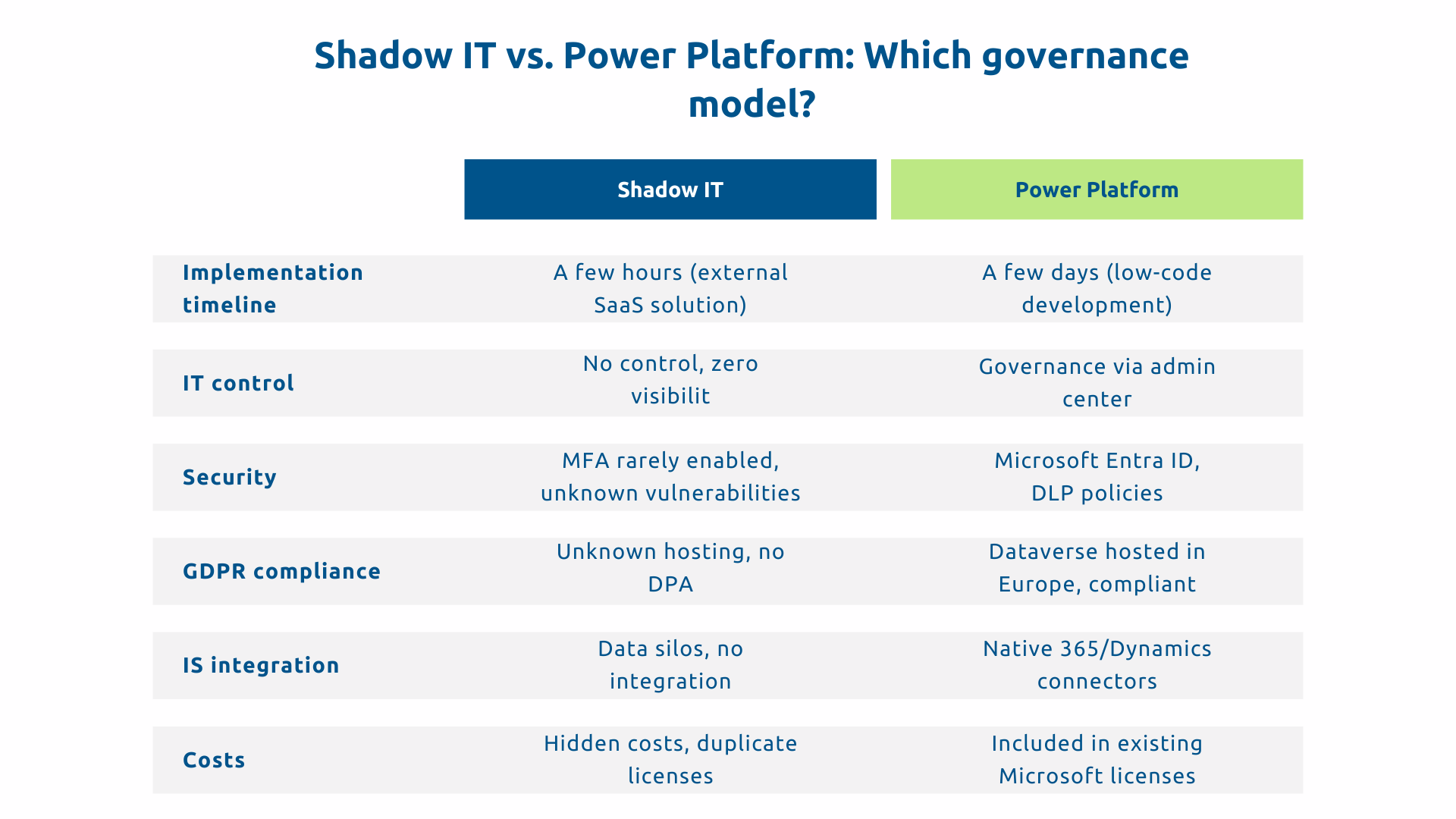
One of the main reasons for shadow IT is the slow development of business applications. Power Platform offers a radical alternative : allow businesses to create their solutions themselves in a governed IT framework.
So, Power Apps builds business applications without coding. Power Automate automates workflows visually. Power BI gives autonomy on data analyses. For simple to medium use cases, development time can range from several months to a few days.
The real advantage lies in the centralized governance. The Power Platform Administration Center allows IT to finely control the environment without throttling businesses.
Data Loss Prevention policies define which connectors can be used together. You allow SharePoint and Dataverse in the same application, but block the simultaneous connection to SharePoint and Gmail, avoiding data exfiltration to personal services.
Approved connectors limit the possible integrations. The IT validates authorized connectors according to their security. The professions maintain a wide range, but within a controlled perimeter.
Native audit Tracks all the creations, modifications, and uses of applications.
Azure and Microsoft 365: a secure and scalable ecosystem
Microsoft 365 covers collaborative needs in a modern work environment:
- Teams;
- SharePoint;
- OneDrive;
- Planner.
Dynamics 365 addresses business applications: CRM, Customer Service, Finance. Azure provides the infrastructure for specific needs: storage, intensive computing, artificial intelligence.
The ecosystem shines above all for its integrated governance tools. Conditional Access in Microsoft Entra ID defines granular access policies based on context: location, device type, user risk level. Microsoft Purview Information Protection automatically classifies and protects sensitive data. Microsoft Defender for Cloud Apps detects and controls which cloud applications are used.
This ecosystem coherence Change the equation. Each component communicates natively with the others, shares the same identity system via Microsoft Entra ID, and respects the same security policies. Shadow IT arises from the complexity of making heterogeneous systems communicate. The Microsoft ecosystem drastically reduces this complexity.
At Askware, we don't just deploy Microsoft tools, we configure, integrate, and govern them so that they meet your business challenges while meeting your security and compliance requirements.
Shadow IT is an opportunity to rethink the relationship between IT and businesses. Keep in mind that the middle way exists: collaborative governance that is based on visibility, dialogue, a clear framework, and agility. Askware supports you in this transformation to transform the energy of innovation into competitive advantage while maintaining security.
Are you noticing the proliferation of unauthorized tools in your organization? Contact our experts to establish a diagnosis of your application ecosystem and co-build a governance strategy adapted to your challenges.




